Web application firewall
Extend the protection of your websites through the WAF
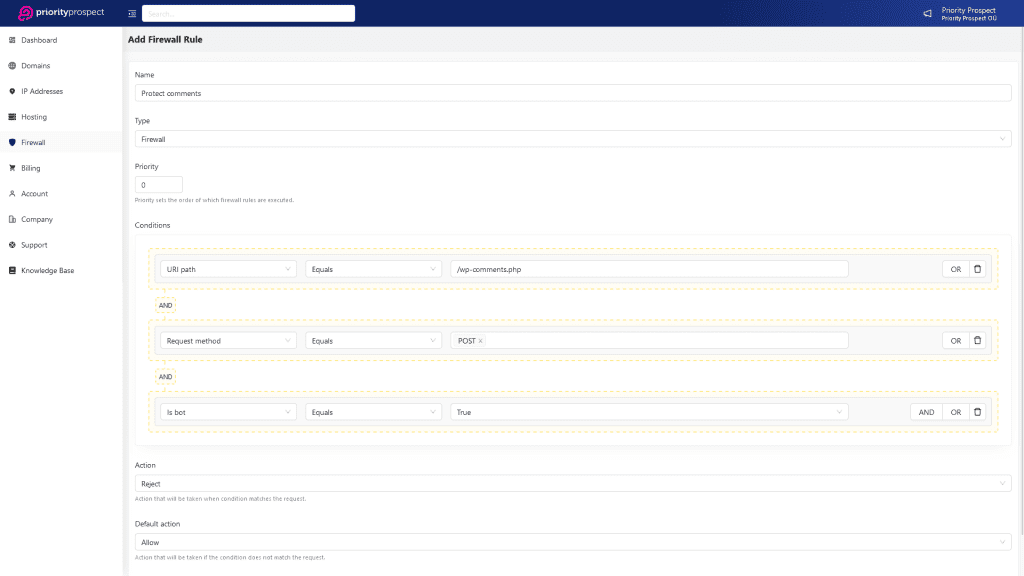
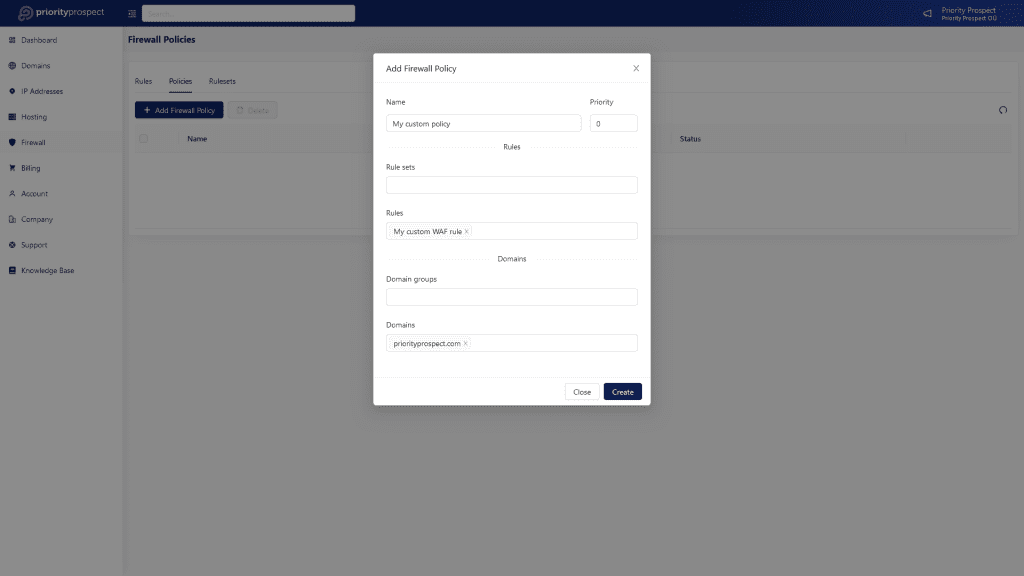
In addition to the cloud firewall, we provide an extra layer of protection for your websites through our Web Application Firewall (WAF). Our WAF actively prevents numerous malicious requests, including hacks, SQL injections, and other common security threats, on a daily basis. Our WAF operates in real-time, continuously monitoring our IP network and promptly responding to any potential threats that may arise. Rest assured that your websites will be safeguarded with proactive security measures in place.